Table des matières
Installation Nextcloud sur CT LXC Debian 10
0 - Création du contenair
- Créez un contenair debian 10
- Faite attention aux privilèges
- Mettez le à jour

- xxx.conf
arch: amd64 cores: 2 hostname: Nextcloud memory: 2048 net0: name=eth0,bridge=vmbr0,firewall=1,gw=xxx.xxx.xxx.xxx,hwaddr=3E:B7:7F:68:5A:31,ip=xxx.xxx.xxx.xxx/24,ip6=auto,type=veth onboot: 1 ostype: debian rootfs: local-zfs:subvol-205-disk-1,size=10G swap: 1024 lxc.apparmor.profile: generated lxc.apparmor.allow_nesting: 1
1 – Nginx
Notre choix se portera sur le serveur HTTP Nginx pour une question de performances. Nginx est reconnu pour ses hautes performances, sa stabilité, son ensemble de fonctionnalités, sa configuration simple ainsi que sa faible consommation en ressources.
1.1 – Installation
Installez le paquet nginx :
apt-get -y install nginx nginx-extra
1.2 – Configuration
Modifiez les directives suivantes du fichier de configuration Nginx /etc/nginx/nginx.conf :
- nginx.conf
user www-data; worker_processes auto; pid /run/nginx.pid; events { worker_connections 1024; use epoll; } http { ## # Basic Settings ## sendfile on; tcp_nopush on; tcp_nodelay on; keepalive_timeout 65; types_hash_max_size 2048; server_tokens off; include /etc/nginx/mime.types; default_type application/octet-stream; ## # SSL Settings ## ssl_protocols TLSv1 TLSv1.1 TLSv1.2; # Dropping SSLv3, ref: POODLE ssl_prefer_server_ciphers on; ## # Logging Settings ## access_log /var/log/nginx/access.log; error_log /var/log/nginx/error.log; ## # Gzip Settings ## gzip on; ## # Virtual Host Configs ## include /etc/nginx/conf.d/*.conf; include /etc/nginx/sites-enabled/*; }
2 – Installation et téléchargement de Nextcloud
- Téléchargez la dernière version de Nextcloud :
cd /var/www wget https://download.nextcloud.com/server/releases/latest.tar.bz2
- Décompressez l’archive Nextcloud :
tar -xvf latest.tar.bz2
3 – Les modules PHP
Nextcloud nécessite certains modules PHP pour fonctionner : Modules obligatoires :
- PHP ctype
- PHP dom
- PHP GD
- PHP iconv
- PHP JSON
- PHP libxml
- PHP mb multibyte
- PHP posix
- PHP SimpleXML
- PHP XMLWriter
- PHP zip
- PHP zlib
- PHP pdo_mysql (connecteur pour MySQL/MariaDB)
Modules hautement recommandés :
- PHP curl : nécessaire pour certaines fonctionnalités de Nextcloud comme l’authentification HTTP
- PHP fileinfo : améliore les performances d’analyse des fichiers
- PHP bz2 : nécessaire pour l’installation et l’extraction des applications Nextcloud
- PHP intl : améliore les performances sur l’internationalisation et les opérations sur caractères non ASCII
- PHP openssl : nécessaire pour accéder aux ressources HTTPS.
Installez les paquets suivants :
apt-get -y install php-cli php-json php-curl php-imap php-gd php-mysql php-xml php-zip php-intl php-imagick php-mbstring
4 – PHP-FPM
Le module PHP-FPM permet la communication entre le serveur Nginx et PHP, basée sur le protocole FastCGI. Ce module, écoutant sur le port 9000 par défaut ou sur un socket UNIX, permet notamment l’exécution de scripts PHP dans un processus indépendant de Nginx avec des UID et GID différents. Il sera alors possible, dans le cas de la gestion de plusieurs applications sur un même serveur, de créer et configurer un groupe (appelé aussi pool) par application. Un pool définit notamment le UID/GID des processus PHP et le nombre de processus minimum, maximum ou encore le nombre de processus en attente à lancer.
4.1 – Installation
Installez le paquet php-fpm :
apt-get install -y php-fpm
5 – Création de la base de données sous MariaDB
5.1 – Installation de MariaDB
Installez les paquets suivants :
apt-get install -y mariadb-server mariadb-client
5.2 – Configuration de MariaDB
Lancez le script de configuration (recommandé) :
$ mysql_secure_installation
NOTE: RUNNING ALL PARTS OF THIS SCRIPT IS RECOMMENDED FOR ALL MariaDB
SERVERS IN PRODUCTION USE! PLEASE READ EACH STEP CAREFULLY!
In order to log into MariaDB to secure it, we'll need the current
password for the root user. If you've just installed MariaDB, and
you haven't set the root password yet, the password will be blank,
so you should just press enter here.
Enter current password for root (enter for none): [Touche Entrée]
OK, successfully used password, moving on...
Setting the root password ensures that nobody can log into the MariaDB
root user without the proper authorisation.
Set root password? [Y/n] Y
New password:
Re-enter new password:
Password updated successfully!
Reloading privilege tables..
... Success!
By default, a MariaDB installation has an anonymous user, allowing anyone
to log into MariaDB without having to have a user account created for
them. This is intended only for testing, and to make the installation
go a bit smoother. You should remove them before moving into a
production environment.
Remove anonymous users? [Y/n] Y
... Success!
Normally, root should only be allowed to connect from 'localhost'. This
ensures that someone cannot guess at the root password from the network.
Disallow root login remotely? [Y/n] Y
... Success!
By default, MariaDB comes with a database named 'test' that anyone can
access. This is also intended only for testing, and should be removed
before moving into a production environment.
Remove test database and access to it? [Y/n] Y
- Dropping test database...
... Success!
- Removing privileges on test database...
... Success!
Reloading the privilege tables will ensure that all changes made so far
will take effect immediately.
Reload privilege tables now? [Y/n] Y
... Success!
Cleaning up...
All done! If you've completed all of the above steps, your MariaDB
installation should now be secure.
Thanks for using MariaDB!
5.3 – Création de la base de données nextcloud
- Tout d’abord, connectez-vous sur l’interface MySQL avec l’utilisateur root et grâce au mot de passe saisi lors de la configuration de MariaDB :
$ mysql -u root -p Enter password: Welcome to the MariaDB monitor. Commands end with ; or \g. Your MariaDB connection id is 49 Server version: 10.1.29-MariaDB-6 Copyright (c) 2000, 2017, Oracle, MariaDB Corporation Ab and others. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. MariaDB [(none)]>
- Créez la base de données nextcloud :
MariaDB [(none)]> CREATE DATABASE nextcloud; Query OK, 1 row affected (0.00 sec)
Tout comme pour la gestion du répertoire nextcloud et pour plus de sécurité, vous allez tout d’abord créer un utilisateur MySQL nextcloud_user dédié à la base de données nextcloud, renseigner un mot de passe (ici : mon_password)et ensuite lui donner les droits sur cette base de données :
MariaDB [(none)]> CREATE USER "nextcloud_user"@"localhost";
Query OK, 0 rows affected (0.00 sec)
MariaDB [(none)]> SET password FOR "nextcloud_user"@"localhost" = password('mon_password');
Query OK, 0 rows affected (0.00 sec)
MariaDB [(none)]> GRANT ALL PRIVILEGES ON nextcloud.* TO "nextcloud_user"@"localhost" IDENTIFIED BY "mon_password";
Query OK, 0 rows affected (0.00 sec)
MariaDB [(none)]> FLUSH PRIVILEGES;
Query OK, 0 rows affected (0.00 sec)
MariaDB [(none)]> EXIT
Bye
6 – Nom de domaine & virtual host
- Créez le fichier suivant /etc/nginx/sites-available/nextcloud :
- nextcloud
upstream php-handler { server unix:/var/run/php/php7.3-fpm.sock; } server { listen 80; listen [::]:80; server_name cloud.ndd.ovh; # Les headers add_header X-Frame-Options "SAMEORIGIN" always; add_header Referrer-Policy "no-referrer" always; add_header X-Content-Type-Options "nosniff" always; add_header X-Download-Options "noopen" always; add_header X-Permitted-Cross-Domain-Policies "none" always; add_header X-Robots-Tag "none" always; add_header X-XSS-Protection "1; mode=block" always; # Remove X-Powered-By, which is an information leak fastcgi_hide_header X-Powered-By; # Path de Nextcloud root /var/www/nextcloud; location = /robots.txt { allow all; log_not_found off; access_log off; } # set max upload size client_max_body_size 512G; fastcgi_buffers 64 4K; # Enable gzip but do not remove ETag headers gzip on; gzip_vary on; gzip_comp_level 4; gzip_min_length 256; gzip_proxied expired no-cache no-store private no_last_modified no_etag auth; gzip_types application/atom+xml application/javascript application/json application/ld+json application/manifest+json application/rss+xml application/vnd.geo+json application/vnd.ms-fontobject application/x-font-ttf application/x-web-app-manifest+json application/xhtml+xml application/xml font/opentype image/bmp image/svg+xml image/x-icon text/cache-manifest text/css text/plain text/vcard text/vnd.rim.location.xloc text/vtt text/x-component text/x-cross-domain-policy; location / { rewrite ^ /index.php; } location ~ ^\/(?:build|tests|config|lib|3rdparty|templates|data)\/ { deny all; } location ~ ^\/(?:\.|autotest|occ|issue|indie|db_|console) { deny all; } location ~ ^\/(?:index|remote|public|cron|core\/ajax\/update|status|ocs\/v[12]|updater\/.+|oc[ms]-provider\/.+)\.php(?:$|\/) { fastcgi_split_path_info ^(.+?\.php)(\/.*|)$; set $path_info $fastcgi_path_info; try_files $fastcgi_script_name =404; include fastcgi_params; fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name; fastcgi_param PATH_INFO $path_info; fastcgi_param HTTPS on; # Avoid sending the security headers twice fastcgi_param modHeadersAvailable true; # Enable pretty urls fastcgi_param front_controller_active true; fastcgi_pass php-handler; fastcgi_intercept_errors on; fastcgi_request_buffering off; } location ~ ^\/(?:updater|oc[ms]-provider)(?:$|\/) { try_files $uri/ =404; index index.php; } location ~ \.(?:css|js|woff2?|svg|gif|map)$ { try_files $uri /index.php$request_uri; add_header Cache-Control "public, max-age=15778463"; add_header Referrer-Policy "no-referrer" always; add_header X-Content-Type-Options "nosniff" always; add_header X-Download-Options "noopen" always; add_header X-Frame-Options "SAMEORIGIN" always; add_header X-Permitted-Cross-Domain-Policies "none" always; add_header X-Robots-Tag "none" always; add_header X-XSS-Protection "1; mode=block" always; # Optional: Don't log access to assets access_log off; } location ~ \.(?:png|html|ttf|ico|jpg|jpeg|bcmap)$ { try_files $uri /index.php$request_uri; # Optional: Don't log access to other assets access_log off; } }
- Activez le virtual host :
ln -s /etc/nginx/sites-available/nextcloud /etc/nginx/sites-enabled/nextcloud
- La nouvelle configuration sera prise en compte après redémarrage des services Nginx et PHP-FPM :
systemctl restart nginx.service systemctl restart php7.3-fpm.service
7 – HTTP2
Je vous conseille vivement d’activer le nouveau protocole HTTP2 qui augmentera la sécurité et la rapidité de votre Nextcloud. HTTP2 permet notamment :
- la compression des headers des requêtes et des réponses qui permet de réduire la bande passante lorsque les headers (comme les cookies) sont similaires
- le multiplexage des requêtes au serveur consistant à faire passer de multiples informations via un seul tuyau de transmission. Ainsi, on économise les multiples connexions entre le client et le serveur. Les requêtes, quant à elles, sont effectuées simultanément par le navigateur. Les requêtes ne se suivent donc plus les unes derrière les autres (HTTP1) et les plus prioritaires (CSS par exemple) ne sont plus bloquées par les moins prioritaires (images par exemple)
- le push des ressources du serveur au navigateur. Désormais, le serveur pourra envoyer l’ensemble des ressources référencées dans une même page (CSS, JS…), avant même que le navigateur n’ait analysé celle-ci.
L’activation du protocole HTTP2 est très simple et consiste en l’ajout de la directive http2 dans votre virtual host du reverse proxy :
....
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name cloud.mondomaine.com;
Une fois la modification effectuée, n’oubliez pas de recharger votre configuration Nginx :
systemctl reload nginx.service
8 – Nextcloud
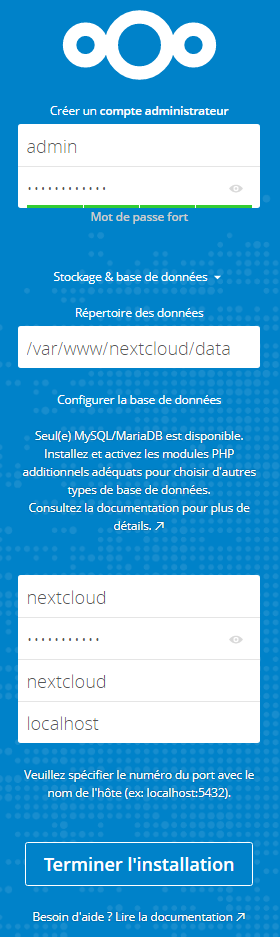
Lancez votre navigateur et rendez-vous à l’adresse suivante : http://cloud.mondomaine.com/. Configurez votre compte administrateur et les informations de votre base de données nécessaires à Nextcloud :
Vérifiez la force de votre protocole SSL/TLS en vérifiant votre Nextcloud sur SSL Labs. Avec une telle configuration, vous devriez obtenir un A+.